EndisProjects
Collection Of Projects List

Splunk-Driven Threat Feed Correlation Engine
A real-time threat intelligence correlation engine that ingests threat feeds from sources like AlienVault OTX and AbuseIPDB, correlates them with internal VPC Flow Logs using Splunk, and generates automated alerts and dashboards to visualize and respond to suspicious activity.

WAF Enabled Multi Layer Web App Firewall
This project showcases the deployment of a layered Web Application Firewall (WAF) using AWS WAF, Amazon CloudFront, and custom + managed rule sets to protect a web application fronted by an Application Load Balancer (ALB). The WAF uses both AWS Managed Rules (e.g., SQLi, IP reputation, Linux OS threats) and custom rules (rate limiting, geo-blocking, admin path protection). CloudFront improves performance and provides an additional security perimeter.
All traffic is monitored and logged to an S3 bucket using WAF logging for audit and tuning purposes.
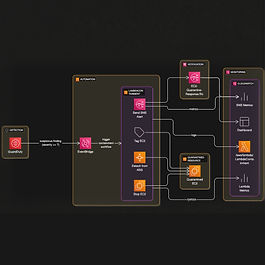
Security Incident Response
This project establishes an automated incident response pipeline using Amazon GuardDuty, EventBridge, Lambda, and SNS. When a high-severity threat is detected by GuardDuty, an EventBridge rule triggers a Lambda function that isolates the impacted EC2 instance, applies incident-related tags, and alerts the security team via SNS.

Centralized CloudTrail Monitoring and Analysis via Splunk
Designed and deployed a centralized security monitoring and event correlation solution by integrating AWS CloudTrail with Splunk using Amazon S3 and SQS. The system enables real-time ingestion, parsing, and visualization of API activity and user behavior across an AWS account. The pipeline is fully automated and security-hardened with IAM best practices and TLS encryption.
