EndisProjects
Description
This project showcases the deployment of a layered Web Application Firewall (WAF) using AWS WAF, Amazon CloudFront, and custom + managed rule sets to protect a web application fronted by an Application Load Balancer (ALB). The WAF uses both AWS Managed Rules (e.g., SQLi, IP reputation, Linux OS threats) and custom rules (rate limiting, geo-blocking, admin path protection). CloudFront improves performance and provides an additional security perimeter.
All traffic is monitored and logged to an S3 bucket using WAF logging for audit and tuning purposes.
Importance
Modern web apps are frequently targeted by OWASP Top 10 threats, IP spoofing, automated bots, and L7 application abuse. This project implements a multi-layered defense strategy using AWS-native services to:
Mitigate common vulnerabilities
Block malicious traffic early
Enable traffic observability without incurring the high cost of services like AWS Shield Advanced
Objectives
- Protect against OWASP Top 10 attacks (e.g., SQLi, XSS, known bad inputs)
- Block login-based brute force and bot attempts
- Rate-limit abusive IPs and paths
- Use CloudFront as a threat-filtering CDN layer
- Log WAF traffic to S3 for audit, tuning, and detection
Tech Stack
AWS WAF (v2)
Amazon CloudFront
AWS S3 (WAF logging)
Terraform (used for infrastructure provisioning)
Amazon EC2 & ALB
Curl (testing), Bash scripting (load tests)
Architecture Overview
CloudFront (CDN) in front of ALB, accelerating and filtering web traffic
Web ACL (multi-layer-waf-v2) attached to CloudFront, containing:
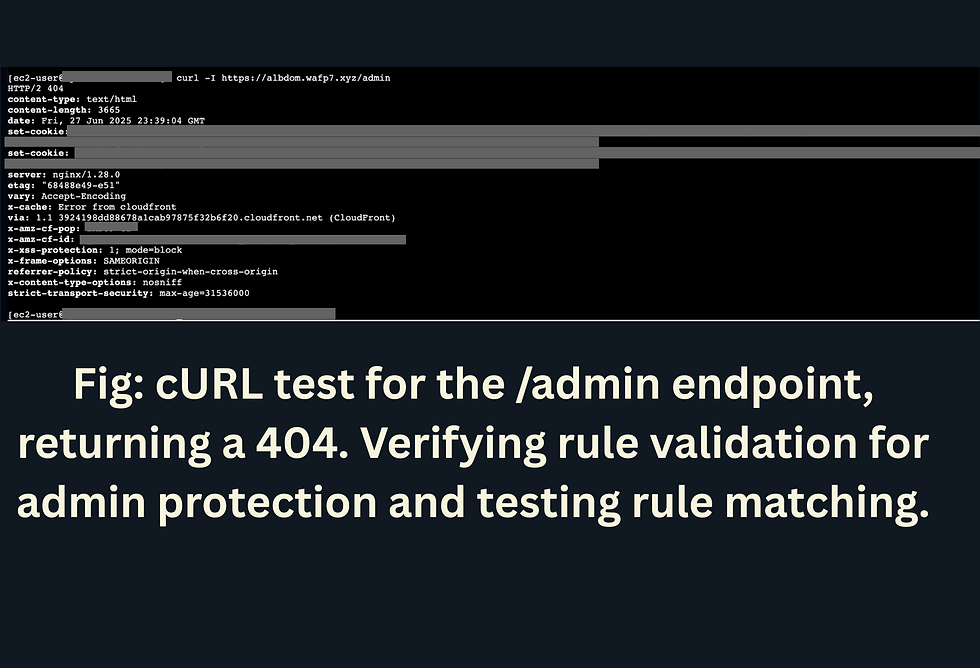
AWS Managed Rules for Admin, SQLi, IP reputation, Linux attacks
Custom rules for country-based blocking, IP blocklists, and path restrictions
Application Load Balancer routes traffic to EC2-hosted backend
S3 logging bucket (aws-waf-logs-4wafp7) stores detailed WAF logs
Manual request simulation verifies XSS, brute force, and SQLi rule effectiveness

Implantation
1. Provision CloudFront and connect to ALB (albdom.wafp7.xyz)
2. Import TLS certificate via ACM and attach to distribution
3. Create Web ACL (multi-layer-waf-v2) and managed rules and
custom rules (BlockedIPs, CountryBlocking, RateLimit2000, PathBlock)
4. Associate Web ACL with CloudFront
5. Enable WAF Logging to S3 bucket
6. Create and apply S3 bucket policy to allow WAF log delivery
7. Simulate SQLi, XSS, brute force and verify logging and blocks
8. Inspect S3 log folder for .json.gz entries and sampled requests
Challenges and Resolutions
Challenge: ExpiredTokenException prevented WAF logging to S3
Resolution: Re-created Web ACL (multi-layer-waf-v2) and reassociated with CloudFront — resolved IAM session cache issue
Challenge: WAF log delivery permission error
Resolution: Adjusted bucket policy with waf.amazonaws.com principal and correct PutObject ACL
Challenge: Need for test verification
Resolution: Used curl scripts to simulate SQLi, XSS, and brute force attempts, confirming rule enforcement
Pictures